Intro
At a customer we got the notification in the vCenter that the certificate was almost expiring. This was about the SSO/STS certificate. Later we found out that also the machine certificates were expiring on each PSC and vCenter that were deployed 2 years earlier. This post will focus on the renewal of the Machine Certificates, if you want to know more about the issue with the SSO/STS certificate, then check out this post.
Check the Expiration of the Machine Certificates
Before you start, make sure that you have created a snapshot on each PSC & vCenter before you going to start this procedure. This blogpost is created after several testing & troubleshooting together with GSS, and at the time writing doesn’t has an official KB article. If you feel uncertain then make sure you create a ticket beforehand and contact GSS. With that being said, let’s start.
The following Command will create a directory in the root, and will display the certificates
in the SSH console:
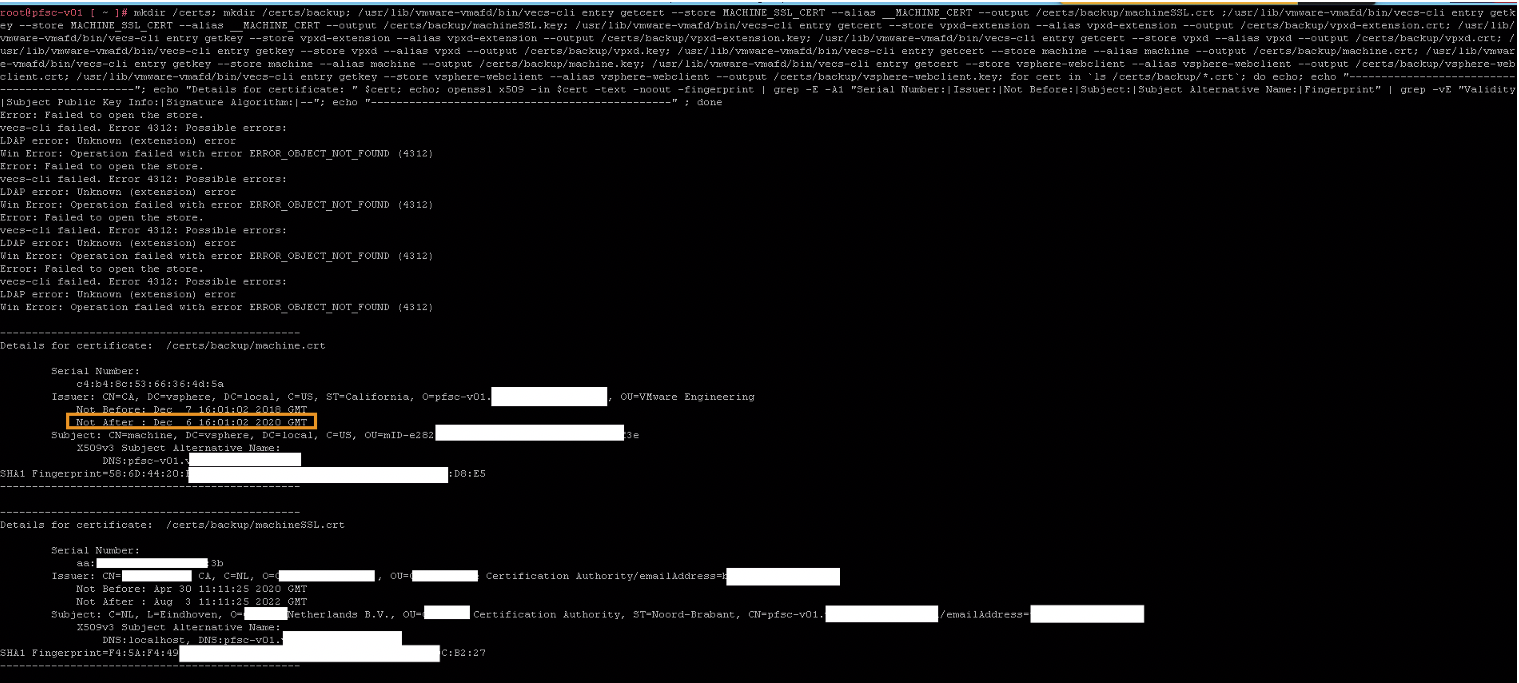
mkdir /certs; mkdir /certs/backup; /usr/lib/vmware-vmafd/bin/vecs-cli entry getcert --store MACHINE_SSL_CERT --alias __MACHINE_CERT --output /certs/backup/machineSSL.crt ;/usr/lib/vmware-vmafd/bin/vecs-cli entry getkey --store MACHINE_SSL_CERT --alias __MACHINE_CERT --output /certs/backup/machineSSL.key; /usr/lib/vmware-vmafd/bin/vecs-cli entry getcert --store vpxd-extension --alias vpxd-extension --output /certs/backup/vpxd-extension.crt; /usr/lib/vmware-vmafd/bin/vecs-cli entry getkey --store vpxd-extension --alias vpxd-extension --output /certs/backup/vpxd-extension.key; /usr/lib/vmware-vmafd/bin/vecs-cli entry getcert --store vpxd --alias vpxd --output /certs/backup/vpxd.crt; /usr/lib/vmware-vmafd/bin/vecs-cli entry getkey --store vpxd --alias vpxd --output /certs/backup/vpxd.key; /usr/lib/vmware-vmafd/bin/vecs-cli entry getcert --store machine --alias machine --output /certs/backup/machine.crt; /usr/lib/vmware-vmafd/bin/vecs-cli entry getkey --store machine --alias machine --output /certs/backup/machine.key; /usr/lib/vmware-vmafd/bin/vecs-cli entry getcert --store vsphere-webclient --alias vsphere-webclient --output /certs/backup/vsphere-webclient.crt; /usr/lib/vmware-vmafd/bin/vecs-cli entry getkey --store vsphere-webclient --alias vsphere-webclient --output /certs/backup/vsphere-webclient.key; for cert in `ls /certs/backup/*.crt`; do echo; echo "-----------------------------------------------"; echo "Details for certificate: " $cert; echo; openssl x509 -in $cert -text -noout -fingerprint | grep -E -A1 "Serial Number:|Issuer:|Not Before:|Subject:|Subject Alternative Name:|Fingerprint" | grep -vE "Validity|Subject Public Key Info:|Signature Algorithm:|--"; echo "-----------------------------------------------" ; done
Which should give the following output:

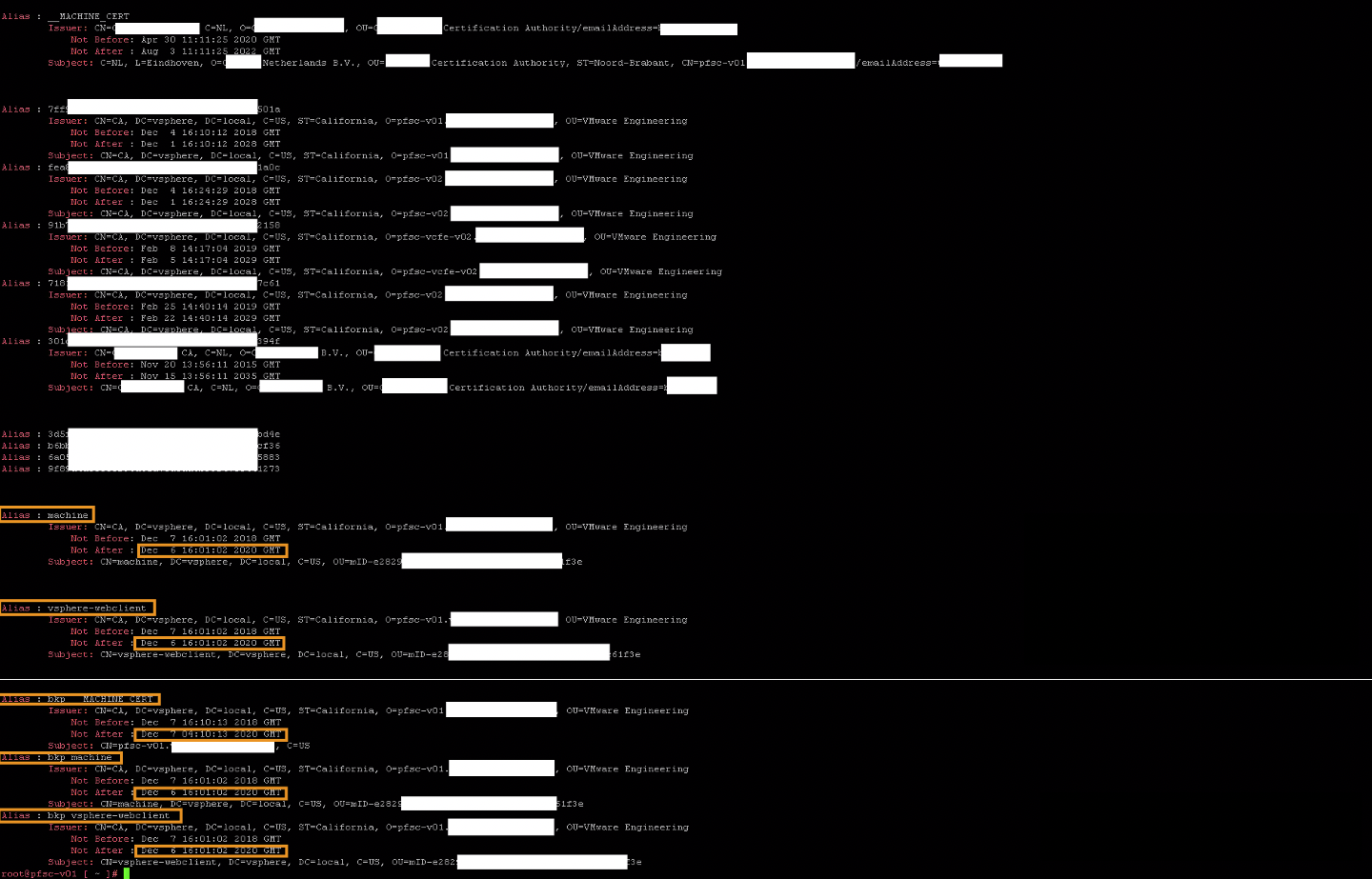
You can also use the following command, which would give a similar output, but with a little more detail. It also doesn’t require you to create a folder. The command is:
for i in $(/usr/lib/vmware-vmafd/bin/vecs-cli store list); do echo; echo; echo; /usr/lib/vmware-vmafd/bin/vecs-cli entry list --store $i --text | grep -E "Alias|Issuer:|Not Before|Not After|Subject:" ; done
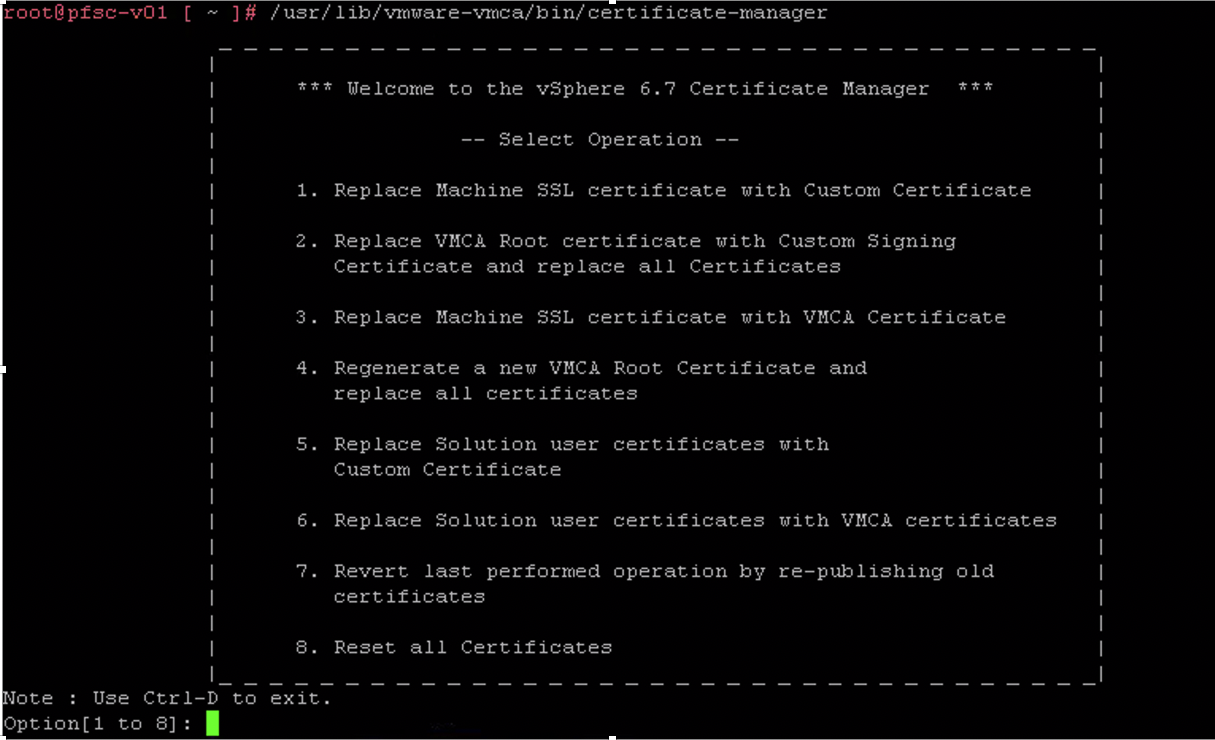
Time to Renew the Certificate
To renew the Solution user certificate we need to use the Certificate Manager.
We will first start with the PSCs, then we will move on to the vCenters.
To do that type down the command:
/usr/lib/vmware-vmca/bin/certificate-manager
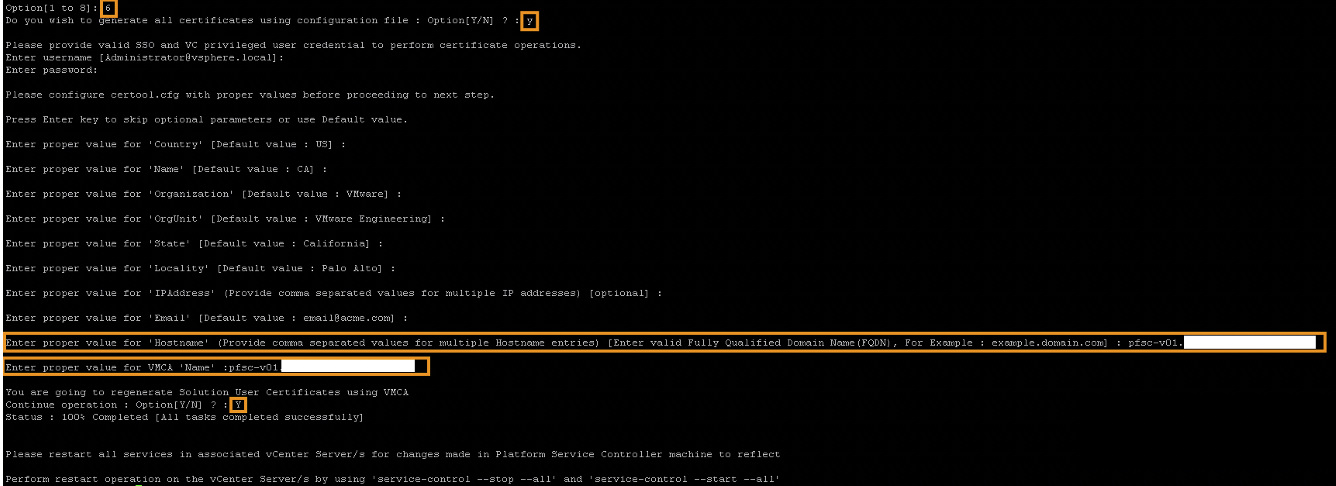
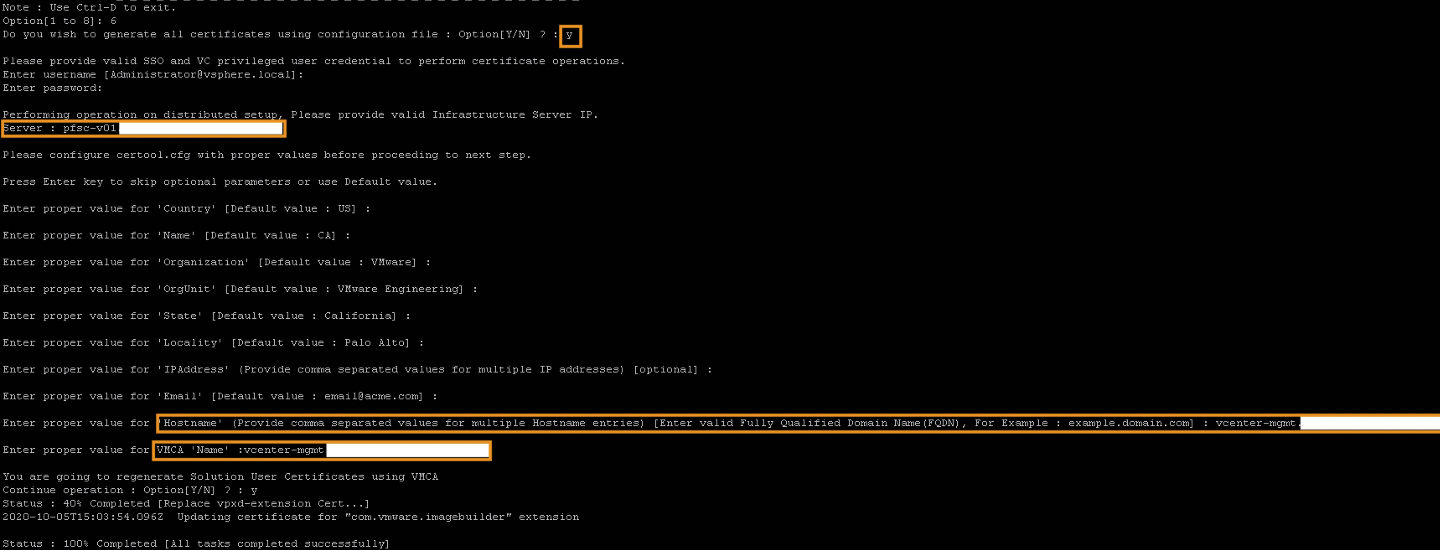
Now Continue with Renewing the Solution user certificates, use Option 6
Type “Y” when it asks to generate all certificates using configuration file
Next you need to fill in the username and password. I used the credentials for the administrator@vsphere.local .
After that you can enter the values for the certificate, but since it is a standard certificate I mostly used the defaults settings. Which automatically are in place when you press enter without filling something in.
At the ending of the cli wizard, you need to fill in the FQDN of the machine that you are generating the certificate on.
Then it asks you one more time if you want to generate the certificate, which you fill in with “Y”.
After that stop and start the services on the psc with:
Service-control --stop --all
Then start it again with:
Service-control --start --all
Once you have done that and everything is started successfully check the status of the certificates again with one of the commands that we previously used.
You should see the date updated.
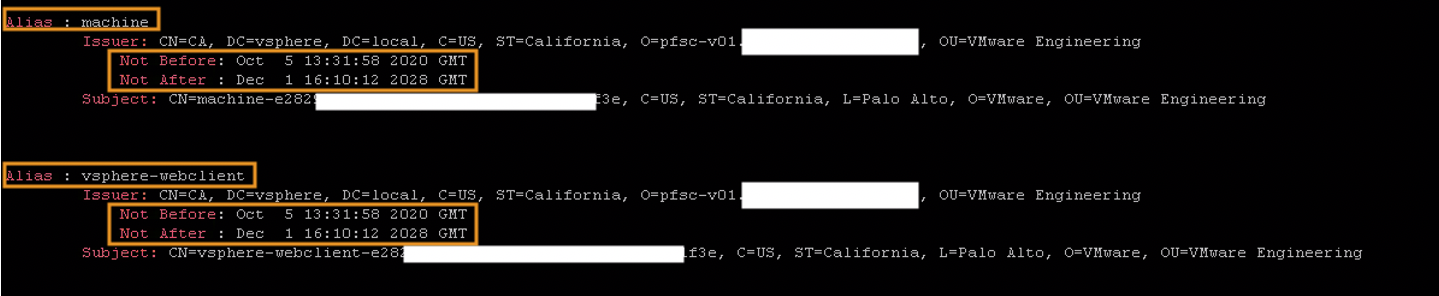
It is possible that a few certificates hold the old date, but in my case, those were backups of the certificates, and thus not needed. Just make sure that you have checked every certificate on their expiration. Do this procedure again for PSC2 if you have it, and otherwise continue to the vCenters.
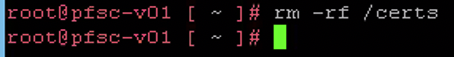
If everything is ok you can remove the output folder (If you have used the first command) for the certificates that we created, by simply typing:
rm -rf /certs
vCenter Procedure
Now before you continue. The procedure for the vCenter is almost exactly the same. Both the check as well as the certificate renewal uses the same commands and input. However, the only difference is when the certificates are being renewed by the certificate-manager. In the vCenter, it asks as one of the first questions “which server it needs to point to”. Which is most of the time psc1 when you are using external pscs. However, this is best to be checked beforehand with the command:
/usr/lib/vmware-vmafd/bin/vmafd-cli get-ls-location --server-name localhost
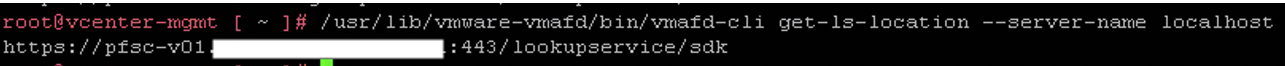
Note down the PSC, because you’re going to need it for renewing the certificate on the vCenter(s).
So check if your vCenter needs to renew its certificate, and if so use the same as previously command:
/usr/lib/vmware-vmca/bin/certificate-manager
Now Continue with Renewing the Solution user certificates, use Option 6
After filling in the username & password, it asks to provide a valid Infrastructure Server IP.
I used the FQDN of the PSC1, which shold be the same host that you found in the previous command. After that I used the same values as for the psc, except that the FQDN was of course the hostname of the vCenter that I was configuring the certificate for.
Restart the services like we did at the PSCs and check if the certificate has been renewed. Do this for every vCenter in your environment.
Hope that this was helpful for you.
Samir is the author of vSAM.Pro & a Life enthusiast who works as a consultant in the field of IT. With a great passion for Tech & Personal Development, he loves to help people with their problems, but also inspire them with a positive outlook on life.
Besides that, he is also a big Sport & Music junky that loves to spend a big chunk of his time on producing music or physically stretching himself.
